Dealing with attacks and unobjective conflicts in science communication
Strategies for dealing with (digital) violence and hate speech are diverse. In addition to our telephone consultation, our guide gives you an overview of possible actions and strategies and provides answers to the most important questions.
1.Who is the target group of the helpline?
Scicomm-Support is an offer for scientists and science communicators who experience attacks and unobjective conflicts due to their science communication.
2.Recognizing the threat situation
Since the Covid-19 pandemic, communicating researchers have not only become increasingly visible in the public sphere, but are also increasingly exposed to hatred online and beyond. In the media, online and offline, but also in the public sphere, researchers who represent results and positions in public are sometimes confronted with serious hostility, threats and insults. Communicators at scientific institutions are also increasingly the target of attacks or unobjective conflicts. Especially in social media, derogatory, insulting and threatening postings are quickly written and sent. For researchers and communicators who are in the public eye, hate can become a threat. For example, when personal data is disclosed (so-called “doxing”) and verbal or virtual threats become serious.
Often there are signs in advance that a threat situation is developing into a situation that requires immediate (re)actions. The key is to assess the situation correctly and react accordingly. Context competence is important here, i.e. analyzing how acute the threat situation is.
If the threat situation is concrete and acute, it should not be made public. Notify the security authorities immediately.
In case of a latent threat situation, support is recommended. You can reach our helpline by phone (0157 923 448 04). For this purpose, it is advisable to involve the communications department of your own institution. Furthermore, your own circle of friends, family and colleagues can provide support. In the case of digital attacks, for example, in the form of counter-speech, objectification and advocacy in social media.
3.Understanding the threat situation
There are no generally applicable criteria for assessing a threat situation. Rather, the classification of diverse and context-dependent factors is decisive.
Here are a few pointers that can help in the assessment:
- How does the threat manifest itself in concrete terms?
-> Are there posts on social media platforms?
-> Are there threatening calls, emails or letters?
-> Do these contain sensitive or private data that is not readily accessible to the public?
-> Are there specific threats against you or your friends and family or people close to you? For example, “dropping by” at your home or one of your lectures?
- Are social media posts such as tweets on X (formerly Twitter) made by a “real” person (Is the profile verifiable, e.g., by means of a clear name or a linked website?). Or are there (increasingly) bots in use?
- Are insults or even threats against various persons or institutions sent out regularly by these respective accounts?
- Is there persistent negative, disrespectful or even campaign-like coverage in the media?
- Are you increasingly recognized in public as a result of this coverage?
- Are you approached by (professional) colleagues about this?
- Are there physical and/or verbal assaults or threats?
Fundamentally: Take every threat seriously! The situation often develops dynamically and it is advisable to take active action. Particular caution is required when threats contain personal data and knowledge about private or confidential processes, such as availability at certain locations. In this case, the threat situation can quickly increase from latent to very concrete. The context and environment in which hate and threats are made must also be considered.
ONLINE AND IN SOCIAL MEDIA:
- Can you tell whether the accounts belong to extremist milieus? For example, through the use of language or familiar codes.
- Is there a recognizable political motivation?
- Do the accounts serve subjects from the so-called “Querdenkenbewegung”, for example?
- Are sources with incendiary content or media campaigns with invective content against researchers cited?
- Are there many or rather few accounts? Are the accounts linked to each other? If this is the case, the impression of a coordinated campaign increases.
Other important components of the crisis strategy are, in addition to professional counseling, support from the personal environment as well as legal counseling and, in the case of concrete and physical threats, alerting the security authorities and the police.
A joint analysis by multiple and different perspectives will make the threat situation more tangible and can be helpful for a possible criminal prosecution.
4.Taking action
Get help and support.
You are not alone! Remember that there are people around you as well as professional contact points such as Scicomm-Support and even the police, who will support you.
Call our helpline.
Scicomm-Support advises communicating researchers and communicators who are exposed to hate and hostility in their science communication. Through our website, we provide extensive information on cases and solution scenarios. In addition, we offer information, support and provide personal counseling by phone.
Please also contact the communication department of your institution.
Are you a researcher or science communicator at a scientific institution? If you are exposed to attacks in the context of your science communication, we advise to also contact your communication department and/or communicate with your colleagues. If this is not an option the experienced consultants of Scicomm-Support are available by phone in any case.
4.1Informing trusted persons and involving the community
People close to you are an essential support for personal resilience and can provide an additional perspective. Confidants offer a safe space for exchange and can provide valuable tips and support in exceptional psychological situations in which the affected person is emotionally compromised.
A trusted relationship is essential: the supportive environment can be close friends, as well as colleagues.
For example, ask the people you trust for the following concrete support:
- Checking your e-mail inbox and file hate messages in a separate folder. One strategy for self-protection may be not to view these messages personally.
- Take screenshots or photos of hate content
NOTE: It is recommended to archive the messages for possible legal action.
If there are several people supporting you, it is recommended to define concrete roles with direct responsibilities and tasks.
4.2General communication and in Social Media
General communication
Attacks on science and the scientific system – e.g. through media campaigns, social media posts or personal contact in everyday life – often aim to assert one’s own interests by discrediting and emotionalizing objective and proven facts.
(Verbal) attacks or threats against the person or their friends and family often aim to intimidate and silence the affected person.
If the attacks and threats are an expression of hostility towards science – perhaps even in unison with an underlying media campaign – these people are usually not interested in a constructive discussion. Nevertheless, depending on the particular situation, it can make sense to express openness and willingness to talk. Sometimes it is possible – online or at larger events with many participants – to win (back) viewers and readers in particular with an objective and level-headed view. Of course, it is essential to insist on a factual and constructive discourse and to always prioritize one’s own safety.
Depending on the situation, different communication strategies are possible to counter hate and incitement. The repertoire ranges from counter-speech, objective confrontation, and ignoring (“Don’t feed the troll”) to criminal prosecution.
First of all, it is important to remain calm, to assess the situation and to evaluate the background and motivation of the harassments.
THIS RAISES QUESTIONS SUCH AS:
- Is the hostility ad hoc or was there a trigger?
- Is it a coordinated campaign?
- If the hostility is coming from a specific person: Do you know the individuals? Are you able to assess their motivation?
- Are attacks – e.g. in the form of social media comments – intended to disrupt or prevent discussions?
Communication in social media
When initiating a conversation or organizing counter-speech, do not engage in endless discussions that lead nowhere. If no objective discussion can be established after three or four exchanged comments and arguments, the other person is not interested in a dialogue.
IN THE CASE OF COUNTER-SPEECH IN SOCIAL MEDIA:
- Call out hate speech as such.
- Hate speech does not necessarily have to be responded to. Posts with disinformation in particular can be reported to the respective platform. In the case of criminally relevant content, legally compliant screenshots (see 4.3) are important and a report or criminal complaint is advisable.
- (Possibly) reply to hate speech constructively – But: avoid arguments, repost and like positive and supportive comments.
- Counter-speech is especially important for bystanders and supports your own position.
- Another option is to deactivate the comment function under your post. However, this should be decided on a case-by-case basis. A deactivation bears the risk of shifting the discussion and renewed accusations (e.g. curtailing freedom of speech). However, deactivating the comment function can also break a hate wave. The Scicomm-Support consultants can give an assessment on this.
- Write your own post and position yourself: This can help to activate your own network, but should be formulated thoughtfully. Precise instructions on how to support and express solidarity are helpful (e.g., call for counter-speech).
- This is also useful for transparency and raising awareness in one’s own community in case of offline attacks. In the case of online attacks on social media, it is also possible to use the comment function for a personal statement.
The German National Institute for Science Communication (NaWik) has prepared detailed strategies for counter-speech. The Amadeu Antonio Foundation’s brochure “Wie kommen wir durch den Shitstorm?” (How do we get through the shitstorm?) presents clear ideas on how to respond to hateful comments.
Hate speech and attacks aim to defame and silence the individuals and institutions involved (also called ‘silencing’). Therefore, publicity and education about these phenomena are particularly important (unless the threat situation is immediately acute). Solidarity and support from one’s own network are essential here.
4.3Documenting the situation
In order to secure incriminating material for a possible charge or criminal complaint, good documentation of the facts is essential. In social media, this includes, for example, legally compliant screenshots of the postings in question and their content. In addition, if possible, the context of the situation from which the threat developed and also the associated comments should be secured.
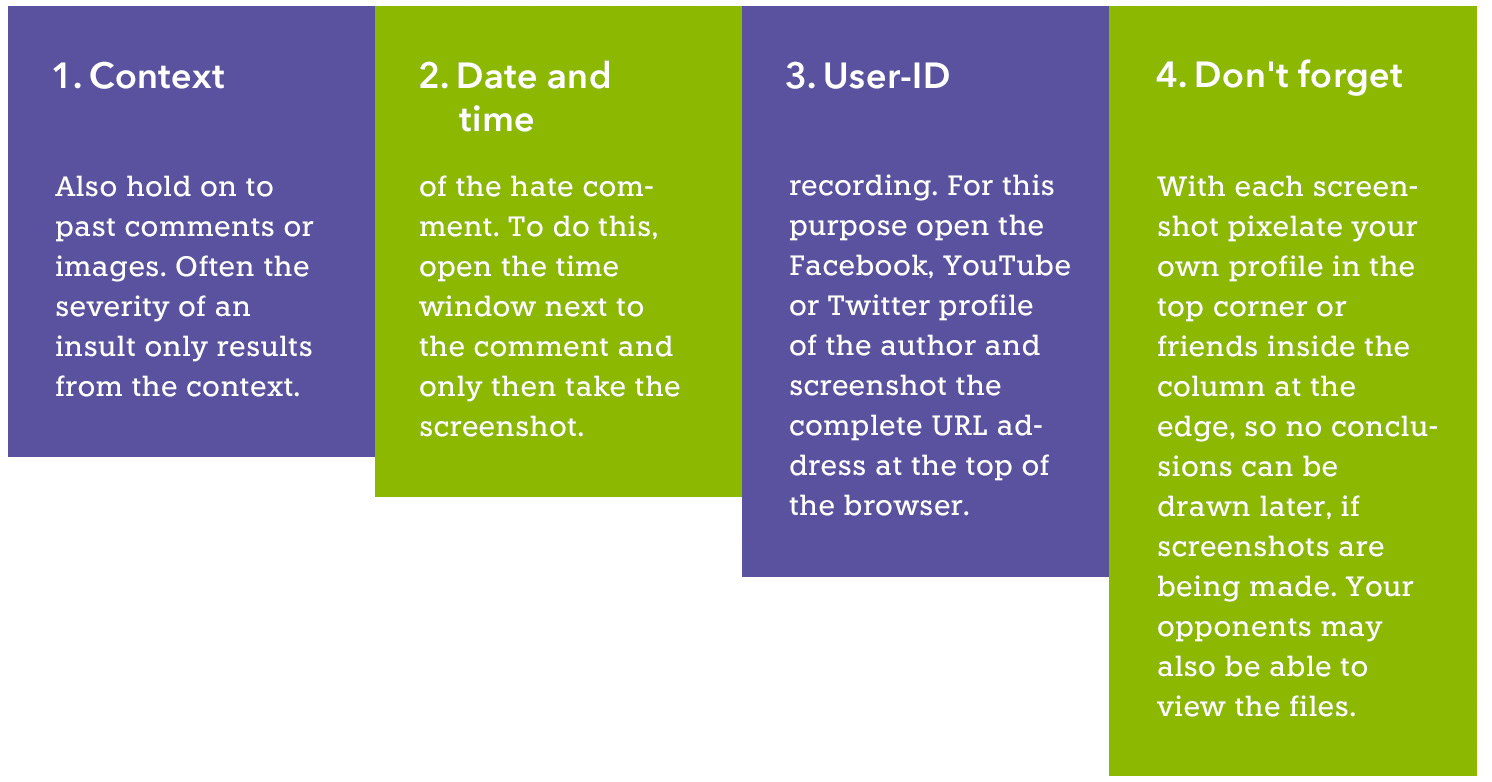
Legally compliant screenshots should contain at least the following information:
- The original posting and the comment in question are readable – the context is important for assessing the offense.
- Date and time (of both the posting and the screenshot itself).
- The platform in question is recognizable from the screenshot.
- Screenshot of the offender’s profile with recognizable direct URL.
- In order to protect bystanders, all other posts, names and pictures readable on the screenshot should be made unrecognizable.
(Please see the PDF for a detailed translation of the graph above.)
After you have taken screenshots, report the posts to the respective platform. If the content is illegal, you have the right to deletion by the platform operator in accordance with the Network Enforcement Act (NetzDG).
In the case of threats and attacks outside of social media, it is advisable to also document the overall situation as comprehensively as possible. But watch out to not put yourself in danger while doing so.
- Take photos and videos of a threatening situation and of the attackers.
- Write down a memory protocol after the threatening situation, e.g. by clarifying five questions: WHO did WHAT, WHEN, HOW, WHERE?
- Photographing, cutting out and documenting newspaper articles.
- In the case of attacks in public spaces: approaching witnesses and securing contact details for later testimony (e.g. students in the lecture hall)
4.4Data protection and privacy
Before and during a threatening situation, it is advisable to perform an online check of your own privacy. Enter your name in combination with personal data such as place of residence, date of birth or job into a search engine and search through the results – even across several pages. This can give you an overview of how easy it is for others to find your data. There is also professional support available here, for example from HateAid, who will conduct a privacy check for you.
For this, it is important to set personal social media accounts to “private” and to secure all accounts, professional as well as personal, with “two-factor authentication”.
Furthermore, it makes sense to obtain an information block for the civil register for yourself and also consider it for relatives as well as employees and/or colleagues. Depending on the respective authority, information blocks can be applied for informally or by submitting an application to the relevant citizens’ registration office. A letter from a counselor is helpful for this. The consultants of Scicomm-Support can provide support in this matter.
4.5Psychological factors
Experiencing hatred, agitation and hostility is an enormous psychological burden. Experiences of emotional and psychological hostility are comparable to those of physical assaults and should not be underestimated.
Therefore, it is advisable to seek personal psychological counseling or coaching. The emotional strain does not only impact the person affected, but also their environment, and should not be underestimated. Professional psychological help can assist in coping with and managing the situation. Our helpline at Scicomm-Support can arrange further psychological support.
If you are able to and if the situation allows it, try to take some time off. Even a few hours or a weekend can be helpful.
IMPORTANT: Attacks and coordinated campaigns against scientists and science communicators are increasingly directed against disciplines with direct social implications. These attacks reflect social lines of conflict and discussions are sometimes undemocratically and unobjectively negotiated. Especially for scientists and science communicators, who are part of the LGBTQIA*-community and/or BiPoC, these attacks can increase and intensify. At the same time, this also means that when hate speech, messages, and (coordinated) campaigns become personal, the person affected is usually not meant personally, but rather serves as a projection surface for these social lines of conflict. Keeping this in mind can help to gain a personal and emotional distance.

Emotional strategies for handling hate posts
- Zoom-out: Don’t take it personally, be aware of the context. At that moment you serve as a projection.
- Radical acceptance: Reality can be very disappointing, especially political and social dynamics – it is a grieving process. What do you need for that?
- Perceive situation/content/emotions: What is this situation doing to me? Which situation would make me feel good? → What do I need in similar situations?
- Process your pain: Every person has their process, it may be writing a diary, publishing blog articles, talking to people about it or laughing about it. Actively search for a way.
- Distraction: Search for positive things in your everyday life that distract you. This helps your psyche to feel safe.
(Please see the PDF for a detailed translation of the graph above.)
5.Law enforcement and legal assistance
Criminal posts and hate comments can be submitted via the internet precincts of the police. In addition, the postings can also be reported to the respective platform. However, this decision must be weighed, because after deletion the authorities can no longer independently preserve evidence. In particular, postings with calls for criminal acts can lead to imitations.
Further information on this can also be found in the “Guide for Threatened Journalists in Germany” by the ‘New German Media Makers’ (Neue Deutsche Medienmacher*innen).
Criminally relevant posts can include insults, slander, defamation or incitement to hatred. Even if you are unsure about the criminal relevance, it is advisable to file a complaint with the public prosecutor’s office. In Germany there are differences between personal offences, which require a complaint to the public prosecutor’s office and offences whose prosecution is in the public interest, such as incitement to hatred or incitement to commit a crime.
A complaint can be filed online with the responsible police, a criminal charge for personal offenses must be submitted to the responsible public prosecutor’s office. This is also possible at a later date. Nevertheless, time limits should be observed. A complaint with the public prosecutor’s office must be filed no later than three months after knowledge of the offense and can only be filed by the individual affected.
Before filing a criminal complaint or pressing charges, it is advisable to seek legal advice. Legal advice helps to professionally assess your situation and the possibilities of criminal prosecution. If desired, Scicomm-Support advisors can arrange and accompany legal support.
6.Helpful contacts and further information
- „Was tun bei Angriffen im Netz? Ein Leitpfad” – Nationales Institut für Wissenschaftskommunikation
- Broschüre „Wie kommen wir durch den Shitstorm?” von der Amadeu Antonio Stiftung
- Ausführliche Informationen zu rechtssicheren Screenshots für die jeweiligen Plattformen von HateAid
- Informationen zum NetzDG
- „Leitfaden für bedrohte Journalist:innen in Deutschland” der Neuen Deutschen Medienmacher*innen
- CORRECTIV – Recherchen für die Gesellschaft
- Der Volksverpetzer
- ARD-Faktenfinder
- Stand Up! von der Arbeitsgemeinschaft Jugend und Bildung e.V.
- „ModSupport – Der Guide für Deine Kommentarspalte” von Civic.net – ein Projekt der Amadeu Antonio Stiftung
- Broschüre „Menschenwürde online verteidigen” von Civic.net – ein Projekt der Amadeu Antonio Stiftung
- „Betreiben Sie Gegenrede” von der Amadeu Antonio Stiftung
- „Onlinerategeber – Social Media-Tipps für die Zivilgesellschaft” der Amadeu Antonio Stiftung
- „Rechtspopulistische Gegenstrategien und wie wir sinnvoll damit umgehen” von Belltower News
- „Anti-Hass-Strategien” der Neuen deutschen Medienmacher*innen
- Anti-Shitstorm-Kurs der Amadeu Antonio Stiftung
- „no:crisis – Notes on critical interaction situations in science communication” der Technischen Universität Darmstadt
